How to Manage Security for Users and Groups
Managing Group Membership
Connectors provide a synchronization process that you can schedule to automatically map source system groups to existing Active Directory (AD) Global security groups or create a copy of the group in Connectivity Hub.
-
Connectivity Hub manages the user membership of these groups so that it matches the membership of the source systems groups.
-
This means that group membership changes are reflected in search results between crawls as frequently as the sync process is scheduled.
Group Mapping Options
Connectivity Hub supports two group mapping approaches to secure the content added to your search index.
-
Since the type is assigned per group, you can use all three in combination.
To determine whether group mapping is appropriate for your organization, use the following table:
| Group Mapping Type | Description | Environment |
|---|---|---|
| Static Group |
A Static Group is a group that maps to an existing Group within Active Directory. In other words, this is a group whose membership is equivalent to the source system.
When this type of group is used to secure an item within the search index, the Group SID value is used.
|
AD and source system groups match, or you have large groups that map to general population groups |
| Native Group |
A Native Group is a group that created and maintained by Connectivity Hub.
|
|
| Expanded Group |
An Expanded Group is a group that is expanded at index time to use the individual user SIDs to secure items within the index.
This is expected behavior for these reasons:
|
Group names do not generally map between AD and source system, and the number of groups is not too large |
Configuring Active Directory Mapping for Your Connector
How to Configure the Active Directory
-
Navigate to Connections and click <name of your Connector> >
 > Edit > Security Directory to see the Security Directory page.
> Edit > Security Directory to see the Security Directory page. -
Click to see the Security Scripts page.

- Group expansion threshold:
- Determines the maximum number of users that must be present to form an expanded group.
- For example, if you specify
10, group that have less than 10 users will be marked as expanded. - All expanded (default): All groups will be expanded. Only users will be specified in the document ACL.
- Determines the maximum number of users that must be present to form an expanded group.
- Click Save to save your changes.
Security Scripts
- Navigate to the Connections page.
- Click <name of your Connector> >
 > Edit > Security Scripts to see the Security Scripts page.
> Edit > Security Scripts to see the Security Scripts page.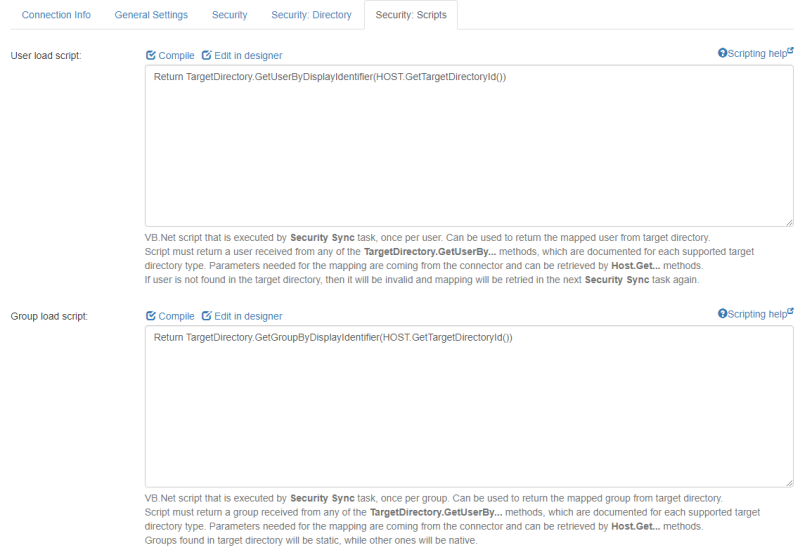
- For additional filtering, write VB.Net scripts to filter users and groups from the source system.
- Each script is called once for each user or group.
- The script cannot return a value.
- You cannot skip users or groups using VB scripting. For more information, go to Scripts.
Note: You cannot skip users or groups using VB scripting.
Overriding Security for Groups and Users
Filter Users and Groups
Select a content source and choose which items are excluded from the crawl when you choose to apply filtering using a VB.NET script.
- Navigate to the Content Sources page.
- Click <name of your Connector> >
 > Edit.
> Edit. - On the page that appears, click the Advanced tab.
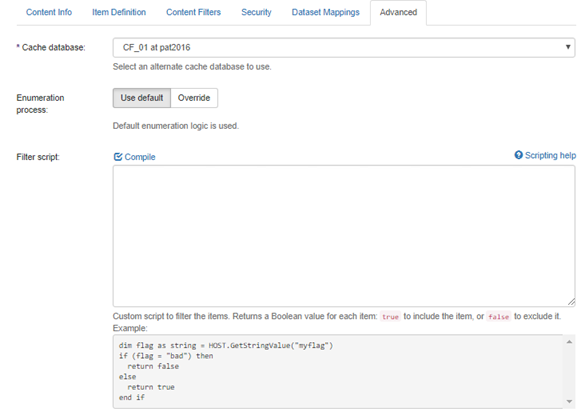
- Filter Script: Enter your filter script using the example in the UI.
- Compile: Click to compile and verify your script.
Make sure that this script returns a Boolean value.
In this case:
-
True =add this user or group -
False =exclude this user or group
Access Control
Access control lets you access, or restrict access to, more groups and users.
- Navigate to Content Sources
- Click <name of your Connector> >
 > Edit. On the Edit WebService/Dataset/... page that appears, click Advanced.
> Edit. On the Edit WebService/Dataset/... page that appears, click Advanced. - Scroll down to access the ACL Script field.
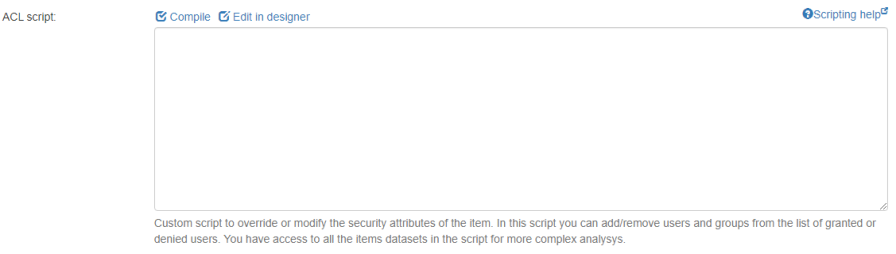
- Click Compile at the top of the field to compile and verify your script
User Status and Crawling
Some of your documents can have security settings that force these documents to be recrawled during an incremental crawl operation although no change is reported for these documents.
-
This is true because we force items that are secured by principals (users or groups) that cannot be located in the security mapping, or that are invalid, to be recrawled.
-
The inactive principals issue warnings in the log files, but do not force items to be recrawled.
There are three types of user status levels:
- Active:
- There are no issues and nothing occurs for these users or for the group.
- Ignore
- Inactive
- A warning is issued in the log file, but no forced recrawl runs.
- Invalid:
- A forced recrawl operation runs.
For example, see the following use cases:
- Invalid + Active status of a principal (user or group):
- This status means that the security was not resolved.
- In this case, the principal is active and might secure items.
- For this reason, the mapping should be resolved (either manually or by improving the security script).
- An item is secured by a principal that was not reported in the list of source system principals (in other words, this item cannot be found in the security mapping for the Connection):
- If the principal is located and mapped during the next security synchronization job, the document is correctly updated in the index and no further recrawl operations run.
- If the principal is located and mapped during the next security synchronization job, the document is correctly updated in the index and no further recrawl operations run.
Note: All principals that appear in Security Mapping as Inactive (Active = false) or Ignored do not force documents to be recrawled.