Certificate-based authentication for SharePoint Online Connectors
When using certificate-based authentication, you must create an App Registration in the organization's Azure Active Directory An identity and access management solution from Microsoft that helps organizations secure and manage identities for hybrid and multicloud environments..
-
Since the connector will potentially crawl millions of records, please make sure to create a dedicated App Registration for the connector.
-
Sharing the App Registration between the connector and another client may lead to excessive throttling for both clients and poor indexing speed.
Application Permissions
The Azure application must be granted one of the following SharePoint Application API permissions, depending on the level of access that you want to enable (see register the Azure application for more information):
-
Sites.FullControl.All: This permission grants Full control of all site collections. This permission is the minimum required as this is the only permission which lets the SharePoint API caller fetch security permissions set on sites.
-
Sites.Selected: This permission only grants access to the specified SharePoint site collections that you will be indexing.
To use the Sites.Selected permission, you must run the appropriate PowerShell script to grant permissions to the Azure Active Directory A directory service for Windows domain networks. A hierarchical structure that stores information about objects on the network. Used to manage permissions and control access to critical network resources. app registration. For more information, see allowing access to only selected sites.
If you are using the Sites.Selected permission, AutoFetch functionality is not supported.
The Azure application must be granted the following Microsoft Graph API Application permissions:
- Member.Read.Hidden: Allows the app to read the memberships of hidden groups and administrative units
- GroupMember.Read.All: Allows the app to read memberships and basic group properties for all groups.
- Directory.Read.All: Allows the app to read data in your organization's directory, such as users, groups and apps.
-
User.Read.All: Allows the app to read all users' full profiles.
- Sites.FullControl.All or Sites.Selected (depending on the level of access you want to enable): Allows the application to either grant full control of all site collections or grant access to a subset of site collections. The specific site collections and the permissions granted are configured in SharePoint Online.
Certificate Requirements
For the following topics you need the signed certificate in PFX and CER formats (created here) as well as the password for the PFX certificate.
Register the Azure Application
- Go to https://portal.azure.com/ and login with Azure Global Admin user credentials.
- Click Azure Active Directory and click on the desired directory.
- From the menu select App Registrations.
- Click New registration to register a new app.
- In the Name field, Enter a name for your app.
- In the Redirect URI section, specify the Application type by select Web or API app from the drop-down list.
- Enter a URI of your choosing. The URI is not used in the SharePoint Online Authorization mechanism.
- Click Register at the bottom of the page.
- Within the app, go to API Permissions.
- Under API Permissions > Add a permission > Sharepoint.
- Select the following permissions for the app depending on the Authentication mechanism used:
- Application permissions> "Sites.FullControl.All" or "Sites.Selected" if required
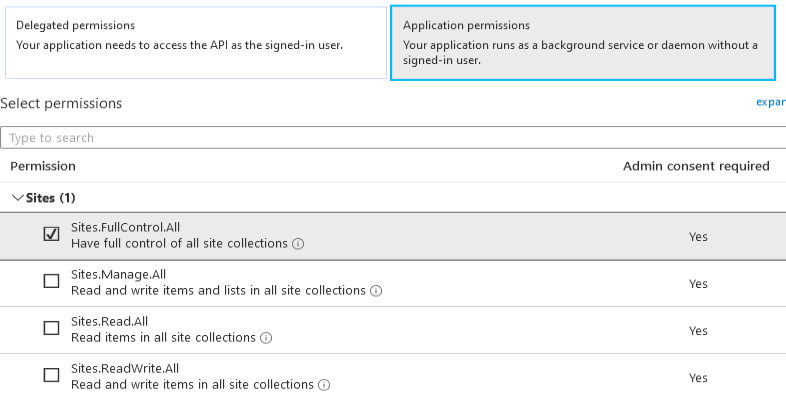
- Application permissions> "Sites.FullControl.All" or "Sites.Selected" if required
- Click the Add Permissions button at the bottom of the screen.
- In the Configured permissions menu, select the Sites.FullControlAll or Sites.Selected permission and click the Grant admin consent button to grant the selected permissions (requires admin rights).
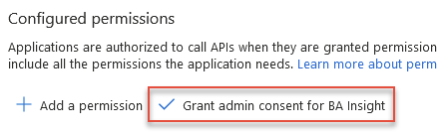
- Repeat this process (Steps 9 through 13) for each of the Microsoft Graph API permissions listed in the Application permissions:
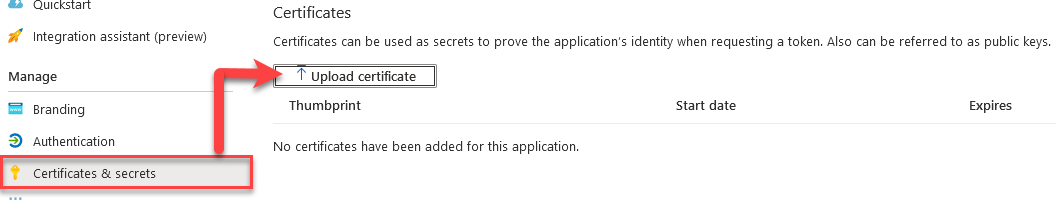
- Open the Azure app you created in the previous steps, above. Under Manage, click Certificates and secrets
-
Add your newly created certificate.
There are multiple methods that can be used to create a certificate. BA Insight recommends the following instructions to create a certificate: How to Create a Self-Signed Certificate.
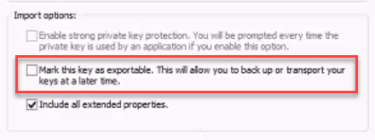
If you use another program, such as IIS, when you export the certificate, ensure you do not mark the key as exportable:
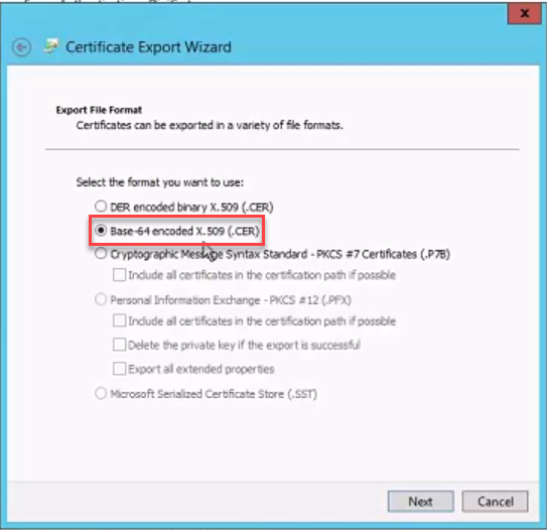
Also, when exporting your certificate using IIS, note that it MUST BE Base-64 encoded:
Allowing access to only selected sites
Note the following before running the PowerShell script
-
To use the Sites.Selected permission, you must grant the Microsoft Graph API permission Sites.FullControl.All to a grantor application.
-
You must be using PowerShell 7 and must have the PnP module for PowerShell installed.
If you want to use the Sites.Selected permission to restrict access to only specified SharePoint site collections, you must run a PowerShell command for the site collections that you want to index. For example:
Grant-PnPAzureADAppSitePermission -AppId 44e4b33e-c6bf-4701-b877-26f642669687 -DisplayName "Upland BA Insight SharePoint Connector" -Permissions FullControl -Site 7c0bec7b-291e-4034-ac8b-e27f5f7306d0Refer to the following table for more information on each parameter of the PowerShell command:
|
Parameter |
Description |
|---|---|
| Grant-PnPAzureADAppSitePermission | This cmdlet adds permissions for a given Azure Active Directory application registration. |
| AppId | This parameter specifies the app ID of the Azure Active Directory application registration. To locate this value for your application registration, in the Azure portal, click Overview and copy the Application (client) ID value. |
| Display Name | This parameter specifies a name for the application permission. This does not need to match the name of the app in Azure Active Directory. |
| Permissions | This parameter specifies the permissions to set for the Azure Active Directory application registration. You must specify FullControl to allow for full functionality of the SharePoint Online Connector. |
| Site | This parameter specifies the GUID of the site collection that you want to allow access to. You can find this value by entering https://<SharePointname>.sharepoint.com/sites/sitename/_api/site/id. |
For more information, see Grant-PnPAzureADAppSitePermission in the PnP PowerShell documentation.
Certificate Installation Options
When configuring the SharePoint Online connector with App Registration and Certificate Authentication, BA Insight supports two certificate installation methods. Both are fully compatible, the correct choice depends on your security model and permissions available to the service account.
| Method | Certificate store | Permissions required | Notes |
|---|---|---|---|
| Recommended (least privilege) | CurrentUser\Personal (CurrentUser\My) | No Local Administrator rights required | rights required Service account imports certificate into its personal store |
| LocalMachine store (legacy/existing deployments) | LocalMachine\Trusted Root Certification Authorities (LocalMachine\Root) | Local Administrator rights required | Remains supported for existing configurations |
Install the Certificate Using the Recommended (Non-Admin) Method
-
Sign in to the server using the service account that will run the connector.
-
Ensure the account is not a Local Administrator.
-
Open the Certificate Manager for the current user by typing certmgr.msc in the start menu.
-
Navigate to Personal > Certificates.
-
Right-click and choose All Tasks > Import....
-
Import your .pfx certificate file.
-
Complete the wizard and verify the certificate appears in Personal > Certificates.
Install the Certificate Using the LocalMachine Store
- Run the Microsoft Management Console (MMC) as an Administrator.
- Add the Certificates Snap-in.
- Expand Trusted Root Certification Authority.
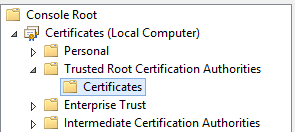
- Use the Actions menu to import your PFX certificate.
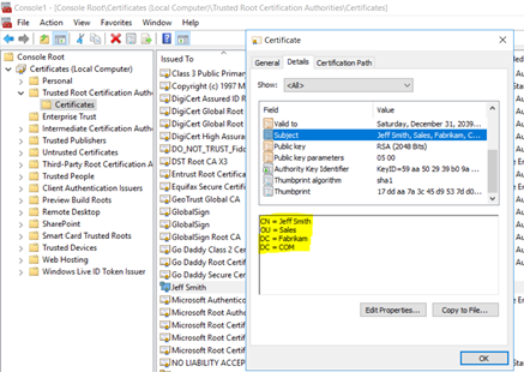
How to Determine the Certificate Distinguished Name
- Run the Microsoft Management Console (MMC) as an Administrator.
- Add the Certificates Snap-in.
- Locate the certificate in the Trusted Root Certification Authority and double-click the certificate name.
- From the pop-up window select theDetailstab.
- Locate the “Subject” field and click on it.
- Identify in the text box below all the distinguished name components.
-
Build the distinguished name based on all the components separated by comma and space characters.
For example: CN=Jeff Smith, OU=Sales, DC=Fabrikam, DC=COMIf you copy your certificate details, as shown below, you must ensure you use syntaxwithout a spaceor your certificate will not work.
CORRECT SYNTAX Example: "CN=Jeff Smith"
INCORRECT SYNTAX Example: "CN = Jeff Smith"