Define Content Security
Use the Content Security form to configure how security is applied to your item.
If you are using the Active Directory A directory service for Windows domain networks. A hierarchical structure that stores information about objects on the network. Used to manage permissions and control access to critical network resources. mapped model and have already synchronized your users and groups, then you must at minimum fill in the Grant SQL statements to ensure that your ACLs are built properly.
The real-time security trimmer section can be utilized in any model, but read Search Security for approaches.
- In Connectivity Hub, open your SQL Content Source Content Sources do the following: Receive data from the Source System via the Connection, Filter the data it receives, Provide the results to the Target, Define the specific search index that contains the content you wish to index (and later search). for editing..
- Click the Security tab.
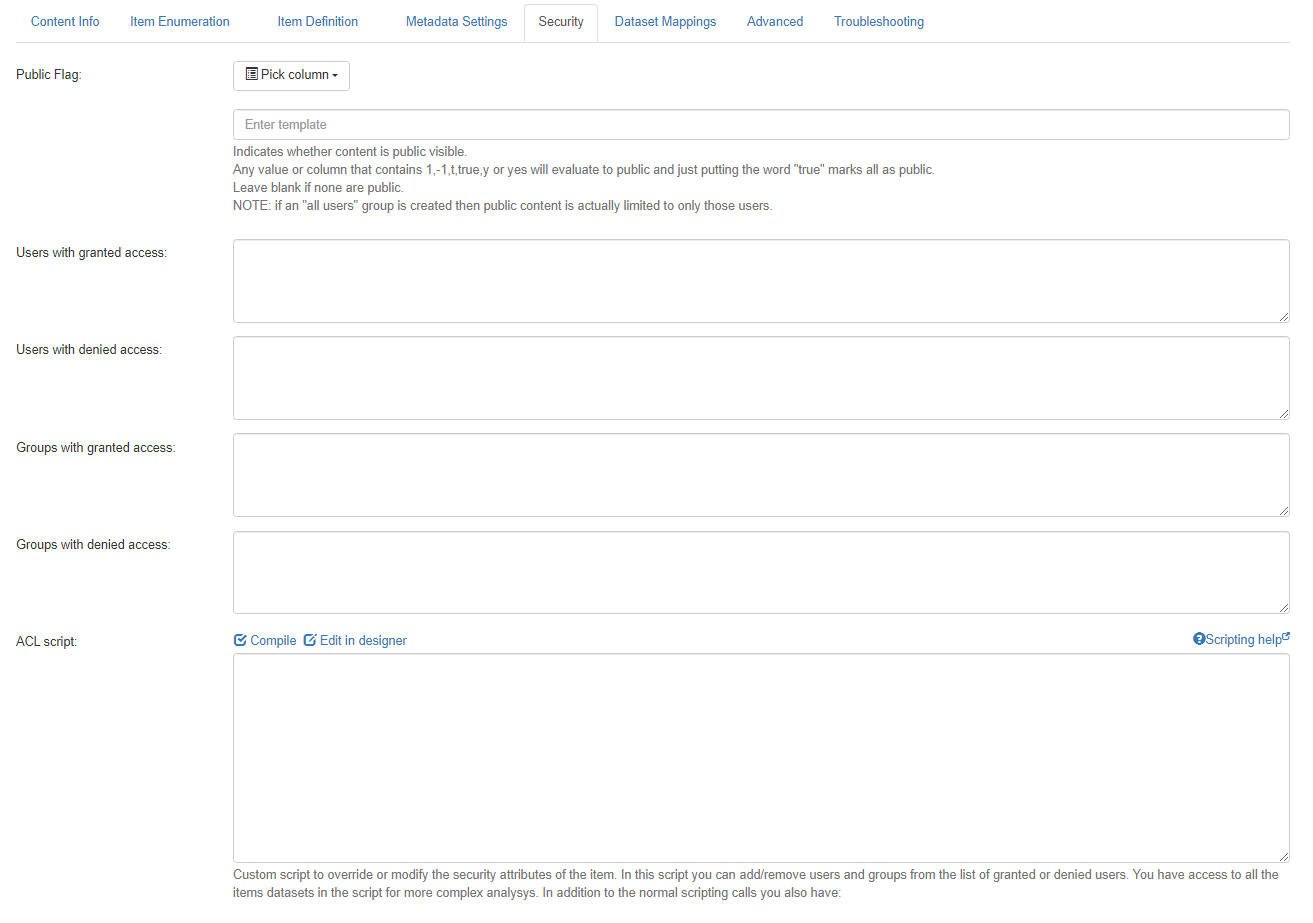
- Public Flag:
- Choose the column that indicates whether content is publicly visible.
- Any value or column that contains
1, -1, t, true, y,oryesevaluate to public, and entering true marks all as public. - Leave blank if none are public.
- The effect of an item being marked as public can vary depending on whether you have created an 'All Users Group'.
- See How to Configure Active Directory for Your Connector.
- Users with granted access:
Enter the SQL statement that returns the list of user IDs that have permission to access this item.- SPW_USERID: Required column.
- [SPW_ID]: Required parameter.
- [SPW_SUBID]: Optional parameter.
- Place the character @S_ or @I_ in front of a variable to indicate String or Integer value.
- For example, @S_SPWID.
- Users with denied access: Enter the SQL statement that returns user IDs of users that are specifically denied access to the system.
- SPW_USERID: Required column.
- [SPW_ID]: Required parameter.
- [SPW_SUBID]: Optional parameter.
- Place the character @S_ or @I_ in front of a variable to indicate String or Integer value.
- For example, @S_SPWID.
- Groups with granted access:
Enter SQL Statement that returns group IDs of groups or roles that have permission to access the item.- SPW_GROUPID: Required column.
- [SPW_ID]: Required parameter.
- [SPW_SUBID]: Optional parameter.
- Place the character @S_ or @I_ in front of a variable to indicate String or Integer value. For example, @S_SPWID.
- Group with denied access:
Enter the SQL statement that returns the list of group IDs that are specifically denied access to this item.
This overrides Grants.- SPW_GROUPID is a required column.
- [SPW_ID] is a required parameter.
- [SPW_SUBID] is an optional parameter.
- Place the character @S_ or @I_ in front of a variable to indicate String or Integer value.
- For example, @S_SPWID.
- For example, @S_SPWID.
- ACL Script:
- Enter VBScript to override or modify the security attributes of the item.
- In this script you can add/remove users and groups from the list of granted or denied users.
- You have access to all the items datasets in the script for more complex analysis.
- For more information, see VB.Net Scripting.
- Enabled Real Time Security:
- Check the box if real time security is enabled.
- When this box is checked, Real Time Security SQL becomes a required entry (see next item).
- Real Time Security SQL:
- This is a required field when real time security is enabled.
- Enter the SQL statement that returns a result if the user is granted access to the item based on the passed in item ID and resolved user ID.
- The value returned does not matter, only the fact that it returned a record.
- Using this model alone results in a single query per item being run.
- Parameters:
- [SPW_ID], (required)
- [SPW_SUBID], (optional)
- [SPW_USERID], (optional)
- Place the character @S_ or @I_ in front of a variable to indicate String or Integer value. For example, @S_SPWID
- Parameters:
- Use this field to provide a custom VB.NET script you can override the default functionality of the real time trimmer and execute the SQL Statements in a more efficient batched way.
- You can also perform real analysis of returned values to determine whether a user is granted access to items or not.
- The global variable HOST is accessible throughout the script to provide various functions.
SampleThis checks the security by running a SQL statement in batch mode for items.
CopyDim sIm()() As String = HOST.GetSecurityItems()
Dim sqlString As String = HOST. GetSecuritySQL()
For i As Integer = 0 To sIm.Length - 1
Dim docId As String = sIm(i)(0)
Dim docVer As String = sIm(i)(1)
dim tSQL as String = sqlString.Replace("[SPW_ID]",docId). Replace ("[SPW_SUBID]",docVer).Replace("[SPW_USERID]", HOST.GetResolvedUserID())
HOST.WriteTrace("SCRIPTSQL:" & tSQL)
Dim ds as Dataset = HOST.FillDataSet(tSQL)
If (ds.Tables.Count 0 AndAlso ds.Tables(0).Rows.Count > 0) Then
Dim fail As Boolean = False
For ii As Integer = 0 To ds.Tables(0).Rows.Count - 1
If (ds.Tables(0).Rows(ii).Item(0).ToString() = "0") Then
fail = True
Exit For
End If
Next
If Not fail Then
HOST.GrantItemAccess(docId, docVer)
End If
End If
NextFor more information, refer to VB.Net Scripting
- Click Save.