Security Trimming in SmartHub and Connectivity Hub
This overview describes how the various systems fit together to ensure that content delivered by both Upland BA Insight SmartHub and Connectivity Hub are security trimmed.
Overview
In essence:
-
Connectivity Hub writes security information into the index
-
SmartHub retrieves security information from the index
The below image depicts the various components used in security trimming and identifies two different flows.
More details provided below in “Workflows.”
SmartHub and Connectivity Hub flows
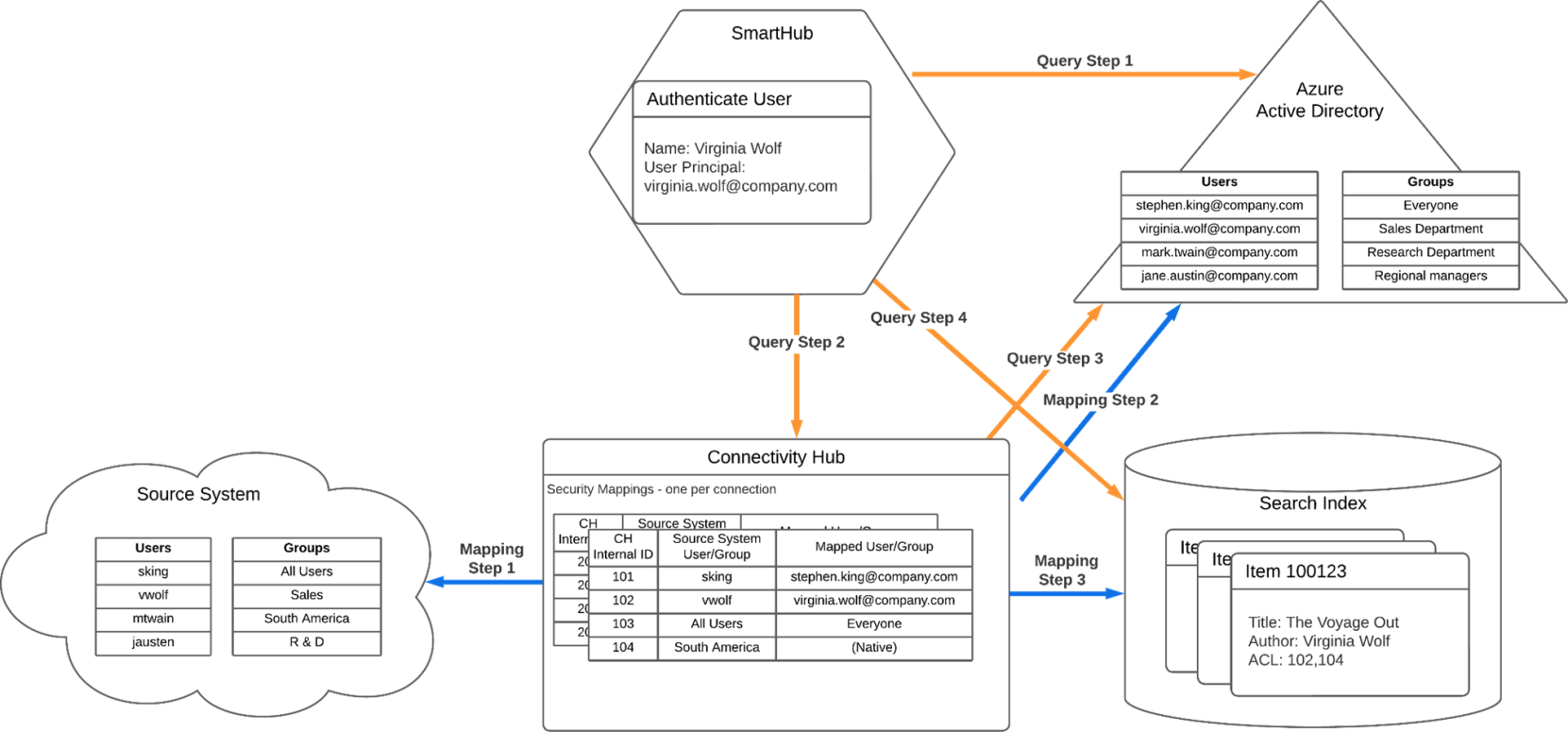
Main Components
The main components:
-
Connectivity Hub
-
The indexing component
-
Functions:
-
Manages the security map
-
Indexes the items crawled using ACLs based on that security map
-
Provides information to SmartHub for individual users
-
-
-
SmartHub
-
The search user interface where user authentication takes place
-
SmartHub has the information about the user who is running the query
-
-
Security Map
-
A part of Connectivity Hub where the users and groups read from the source system are mapped (associated with) corresponding users and groups from the Target Directory (Azure AD in this example.)
-
-
Azure Active Directory
-
The directory server
-
Used for this example as the target directory in Connectivity Hub and the authentication provider
-
-
Search index
-
The index where the searchable items are stored
-
This could be any of the supported indexed
-
-
Source System
-
The system that is crawled, and the security of the searched items is expected to match this system
-
Workflows
See the image above, SmartHub and Connectivity Hub flows.
-
The two workflows:
-
Mapping flow
-
Query flow
-
Mapping flow, marked by blue arrows
-
The “Mapping” flow is driven by Connectivity Hub
-
This flow takes place while indexing the content so that it is properly indexed and prepared for security trimming
Query flow marked by orange arrows
-
The “Query” flow is driven by SmartHub
-
This flow takes place at query time
-
Retrieves only items that the user running the query should see
Flows
|
Mapping Flow |
Query Flow | |
| Step 1 | During the security sync: the connector reads the users/groups from the source system. | The user accessing SmartHub authenticates against the authentication provider |
| Step 2 |
During the security sync: Connectivity Hub matches the users and groups found in the source system with users/groups in the target directory. For groups, if a match is not found in Active Directory, Connectivity Hub stores the members of that group (Members identified from the source system) in a “native” mapping. |
At query time, the “Advanced Security Module” stage queries Connectivity Hub with the user’s info, to get that user’s group memberships. |
| Step 3 | At crawl time: The security descriptors for the items being crawled are read, and the corresponding internal Connectivity Hub identifier is written into the ACL property for that item in the index. | While retrieving the user’s group membership, Connectivity Hub calls the Target directory to find current directory group memberships. |
| Step 4 |
Finally, when sending the query to the search index, the query contains information to insure only items with an appropriate ACL list are returned:
|