How to Configure Token-based Authentication
About Authentication
We exchange the user token that is currently valid for SmartHub with a token that is valid for the Azure app assigned to Elasticsearch.
Note! Token Based Authentication works only with Azure Active Directory authentication configured in SmartHub.
For more details about how to configure Azure Active Directory in SmartHub, go here.
Prerequisites
- SmartHub configured with Azure Active Directory
- An app registered in Azure for Elastic Authentication
Grant the app permissions
You must grant the SmartHub app registration permissions in order to consume the Elastic app.
For more details about this procedure, go here.
- Log in to your Azure portal as an administrator:http://portal.azure.com.
- Click Azure Active Directory → App registrations → App applications.
- Search for application used for SmartHub Authentication.
- Click the "API permissions" entry from the left side navigation menu.
- Click Add a permission:
- Click "APIs my organization uses" and search for "Elastic App."
- Click "Add permissions."
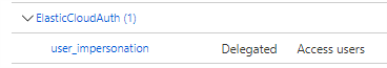
- Now your app should be under "Configured permissions" from SmartHub Authentication app.
- Click Grant admin consent (the button near to the App a permission)
Elastic Backend Configuration
- Choose "TokenBased" from Authentication Mode drop-down menu.
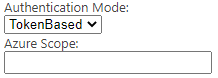
- Add Azure Scope from Elastic Authentication app
- To obtain Azure Scope from an Azure app, perform the following steps:
- Log in to your Azure portal as an administrator:http://portal.azure.com
- Select Azure Active Directory → App registrations → App applications
- Search for the application used for the Elastic Authentication app
- Select Expose an API → Add a scope
- Add a scope name → Choose who can consent → Add a consent display name → Set state on Enabled
- Click "Add scope."
- To obtain Azure Scope from an Azure app, perform the following steps: