Obtaining a certificate
Certificates are files that uniquely identify people and resources on the Internet. They are required to enable secure, confidential communication between two entities.
For production purposes, it is highly recommended that you obtain a proper certificate issued by an official Certificate Authority (CA).
Certificates can be obtained from many different commercial parties. If you use certificates for other applications, you are likely already dealing with a Certificate Authority. Alternatively, you may turn to a service like Let’s Encrypt, which provides an easy way of obtaining an official certificate for free (the drawback is, you will have to renew the certificate more frequently).
Certificates are associated with a specific domain, so this will usually be handled by the person managing that domain, typically someone in your IT department.
Sometimes a server has not been added to a domain - the OL Connect Server, for example -, or a local domain is used for internal servers. In cases like these, the IT department could either manage and create their own certificates, or use self-signed certificates.
Creating self-signed certificates
Self-signed certificates are public key certificates that are not issued by a trusted certificate authority. Because of this, they are more used in testing than for actual deployment.
The easiest way to create a self-signed certificate is to simply go to an online certificate generator such as selfsignedcertificate.com. Just type a server name, domain, or even just localhost, and download the certificate and its private key.
Alternatively, you can create your own certificate locally by using OpenSSL. Getting OpenSSL may be a bit of a pain; you have to either compile it yourself, or get it from a third party that you trust. A nice source can be Git, as that has OpenSSL bundled.
Creating the certificate and private key is a single command. For example:
openssl req -x509 -sha256 -days 365 -newkey rsa:2048 -keyout privateKey.key -out certificate.crt
Or like this, if you don’t want a password for the key file:
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout privateKey.key -out certificate.crt
You could also create self-signed certificates directly with Windows PowerShell, but you would still have to use OpenSSL to extract the certificate and the corresponding key from the .pfx file that you would get from the store.
Note: Keep in mind that when using a self-signed certificate, clients (e.g. browsers) might need to be told to trust it.
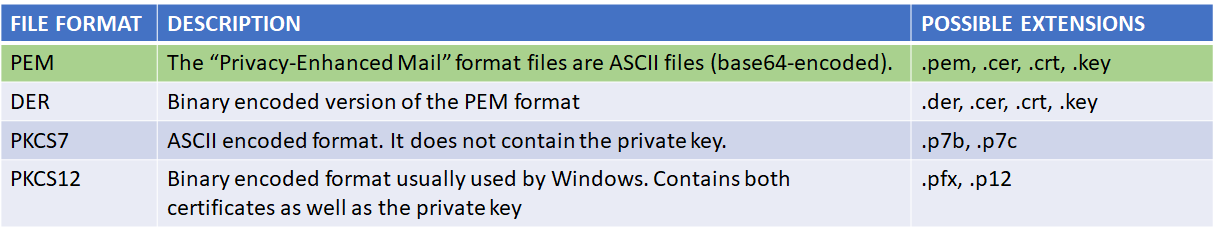
Certificate file format
Once obtained, the format of the certificate file received may be either one of these four formats: PEM, DER, PKCS7 or PKCS12.
Only private key files in the PEM format (ASCII base64 encoded) can be used to set up secure communication in Workflow.
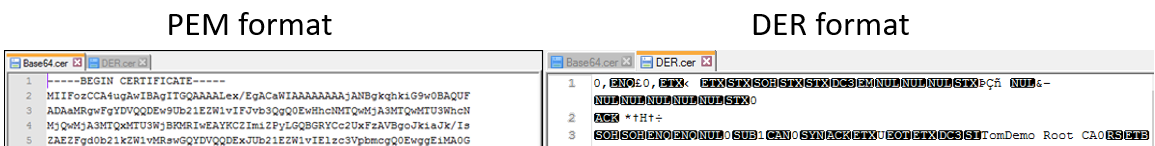
Tip: In a text editor, all characters in a PEM file are displayed as text, whereas some characters in a DER file will be displayed as symbols.
Converting a file to PEM
If your file(s) is (are) any other format than PEM, follow these steps to convert your file(s) to PEM.
- Get the OpenSSL software library which you will use to convert your file(s) into PEM format. A nice source can be Git, as that has OpenSSL bundled.
- Once installed, right click on openssl.exe and choose 'Run as Administrator' (a command window will appear).
- Use the appropriate command below for the type of conversion required after changing the green highlighted text for the name of your file:
- Convert DER to PEM:
openssl x509 -inform der -in certificate.cer -out certificate.pem - Convert PKCS7 to PEM:
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.cer - Convert PKCS12 to PEM:
openssl pkcs12 -in certificate.pfx -out certificate.cer -nodes