Security Profiles define the access rights assigned to users within an organization based on their level of responsibility. These roles control what users can access and perform in the system, ensuring they have the appropriate permissions to fulfill their duties effectively.
While the out-of-the-box Security Profiles come with default access rights, you can customize these roles to suit your organizations specific needs. This includes configuring new Security Profiles, editing existing ones, or copying them to create similar roles with minimal effort.
We strongly recommend avoiding direct modifications to the out-of-the-box Security Profiles. These predefined roles are designed to provide default configurations that align with standard organizational needs. Instead, consider copying the out-of-the-box Security Profiles and customizing the copies as needed. By doing so, you preserve the original roles as a reference and ensure they remain intact for comparison or future use.
When you copy a Security Profiles, the following components are duplicated from the original profile to the new one:
- Associations: Home pages and Dashboards linked to the original Security Profile.
- Menu Setup: The menu configurations and structure.
- Tab Security: Permissions related to accessing specific tabs.
- Security Profile Access settings: All access rules defined for the source profile.
This article details how to copy a Security Profile.
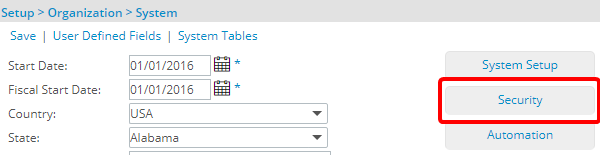
- From the Icon Bar click Setup
 .
. - From the Navigation Menu click Organization.
- From the menu click System.
- From the System page click the Security button to access the Security setup page.
- Click the expand button (
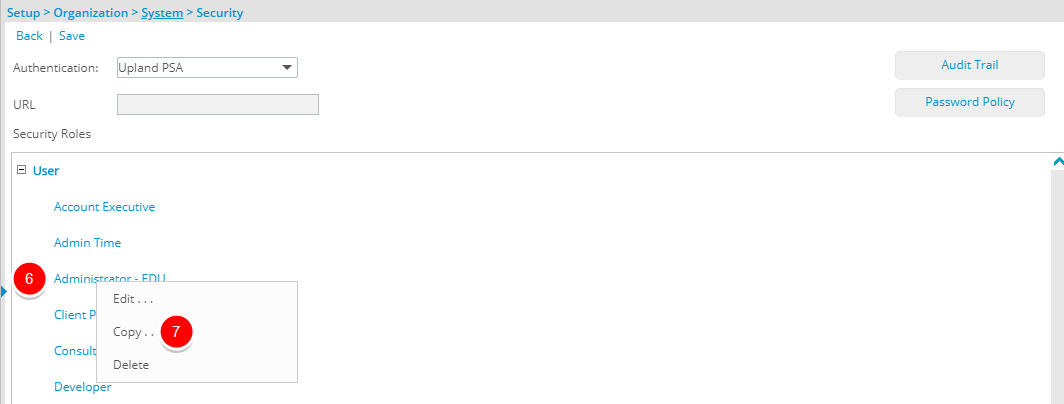
 ) located against a User Security Role Placeholder, if applicable to view the available Security Roles.
) located against a User Security Role Placeholder, if applicable to view the available Security Roles. - Right-click the Security Profiles you wish to copy.
- From the context menu click Copy.
- Enter a name for the newly copied Security Profile.
- Click Save to apply your changes.
Note: All Associations (Home pages and Dashboards), Menu Setup, Tab Security and Security Profile Access settings are copied from the source Security Profile to the copied Security Profile.