Sign In to PowerSteering - SSO
Single sign-on (SSO) is an authentication process that allows users to log into multiple software systems with a single identification. Many organizations choose to enable SSO because it only requires users to enter their login credentials (username and password) once in order to access all of their applications. This creates a simpler sign in process for users as well as a safer one.
When users have too many passwords, they become easy to forget. This causes users to create more common or weak passwords that make it easier for malicious actors to steal data. In fact, approximately 81% of company data breaches occur due to stolen or weak passwords.
Example: Without SSO, a user might have to sign in to multiple applications during the day. Also, they might have to remember a multitude of passwords that must be used for each of these applications, which leads to a higher risk of forgetting certain credentials and getting locked out of applications. They might alternatively create much weaker passwords to make it easier to remember, which can result in stolen data. With SSO, users only need to enter one password to access all of their software applications. This results in a safer, simpler login process.
PowerSteering can be enabled for SSO. Administrators should reach out to their PowerSteering representative if this is something that they would like to explore.
Note: PowerSteering users on SSO sites sometimes have trouble accessing the RESTful API documentation. If you are interested in implementing SSO, please inquire about this to your PowerSteering representative.
This page covers the following topics:
Logging in to PowerSteering using SSO
Users who use an SSO version of PowerSteering will not sign in to the application the standard way. Instead, they will be prompted to enter their credentials into a third-party application upon opening PowerSteering. They will be given access to PowerSteering once they are authenticated by this application.
Note: SSO applications often require multi-factor authentication (MFA). This means that the user might have to take another step before receiving access to all of their applications. For example, many SSO applications will require users to download an app on their smartphones. When users enter their credentials, they will be prompted to open the app on their phone and approve the login to confirm that they are signing in as themselves.
SSO users will notice differences within PowerSteering when they edit the user profile. Specifically, they will not be able to change the username and there will be no password fields under the "Basic Information" section of the page:
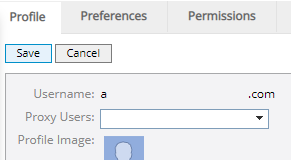
This is because these credentials will be separate from PowerSteering; they will belong to the SSO application that is used to sign in.
However, users on SSO sites will see editable password fields on this page if they have permission to use the PowerSteering REST API (this includes administrators and users with API Context permissions). This is because the API requires a username and password for authentication. This will be clarified next to the fields:
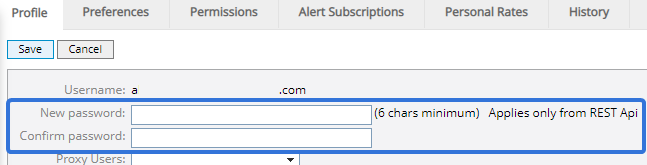
It is important for SSO users to understand that this password will NOT be used to sign in to PowerSteering. If this password differs from the password used to sign in to the SSO application, it will not act as a substitute. It is only to be used (along with the displayed username) for REST API authentication.
Common SSO Problems
SSO provides users with a convenient way to access multiple applications with a single set of login credentials. However, users and administrators should be aware of the errors that commonly occur before deciding to implement it:
Note: These are general issues that may occur with any SSO configuration. Be sure to speak to your trusted SSO provider about more specific issues that could arise.
-
Expired SSO certificate: Expired certificates are one of the most common reasons that users are prevented from using SSO to sign in to their applications. Strong SSO tools authenticate users through digital certificates. Certificate-based authentication integrates with an SSO solution and provides identity context to help monitor who is connecting to your network using what device. However, these certificates can expire after a set period of time. When this occurs, SSO sign in may fail, citing unsuccessful authentication as the problem. If this occurs, reach out to your PowerSteering representative and inquire about the certificate.
-
Security vulnerabilities: SSO can cause security concerns if not implemented correctly. If a weak SSO process is compromised, an attacker could gain access to multiple applications, increasing the impact of a single security breach. Make sure your organization is using a trusted SSO provider to prevent these attacks from being successful. Also, ensure that each user creates a strong password to prevent attackers from accessing their data.
-
Provisioning and deprovisioning challenges: Managing user accounts across various applications can be complex. When a user joins or leaves an organization, ensuring proper provisioning and deprovisioning across all integrated applications becomes crucial. Make sure your SSO provider has a process for onboarding and outboarding users.
-
User education: SSO should ideally enhance the user experience, but if users are not correctly informed about the process, it could lead to confusion or difficulties for users when accessing applications. For example, users might not be used to setting up two-factor authentication on their smartphones. Ensure that users can access informational resources to help them understand how to properly use the SSO configuration.
-
Single point of failure: Since SSO relies on a central authentication system, any disruption in that system can prevent users from accessing multiple applications. Make sure to use a trusted SSO provider and keep track of when your digital certificates are set to expire.