Administrators can implement the Kerberos authentication protocol in
conjunction with the
Kerberos Authentication
Kerberos is a network authentication protocol designed to provide robust authentication services and greater security for users and client/server applications. Authentication is the action of verifying a user’s identity or process. The use of a password is a typical example of authenticating a user. However, with Kerberos Authentication, the use of a password is removed from the equation and other authentication processes come into play like delegation and impersonation.
Kerboros Delegation and Impersonation
It is typical for one server to communicate with another server to accomplish a task on a client's behalf. The scenario where a server is given the authority to act on a client's behalf is known as Delegation.
The following questions need to be addressed from a security standpoint regarding delegation.
-
What will the server be allowed to do when acting on the client's behalf?
-
What identity will be used by the server when it communicates with other servers on behalf of a client?
In response to these questions, the server can impersonate (pretend to be) the client if the client grants authority to the server. This is known as Impersonation. The server is given access only to those resources that the client has permission to use when impersonating the client.
Kerberos Delegation/Impersonation and the Server
The server is given permission to impersonate a user by capturing only usernames at designated devices for the delivery of documents to network share folders. Passwords are not captured or used by the server.
Kerberos Delegation is used with network share folder workflows and the FileScan connector.
More about Kerberos
See the following resources for more information about Kerberos Authentication, Delegation, and Impersonation.
Before you begin
As an administrator, you must complete the following tasks to implement Kerberos Delegation at your company.
-
Configure Windows for Kerberos Delegation
-
Apply Kerberos Delegation to a Network Share Folder workflow
The server captures the username during authentication at the device, impersonates the user and delivers jobs to the network share folders as the authenticated user.
Administrators must use Windows Administrative Tools > Active Directory Users and Computers to configure Kerberos Delegation.
Access Windows Administrative Tools > Active Directory Users and Computers
Ensure Active Directory Users and Computers is available on the domain controller you are using. A domain controller is a server computer that responds to security authentication requests within a Windows domain.
Note: You will need to install Active Directory Users and Computers; if it is not available, to configure Kerberos Delegation.
To access Windows Administrative Tools > Active Directory Users and Computers
-
On the Start menu, select Windows Administrative Tools or type Administrative Tools in the Taskbar Search box.
-
Select Active Directory Users and Computers.
Windows Active Directory Users and Computers at a Glance
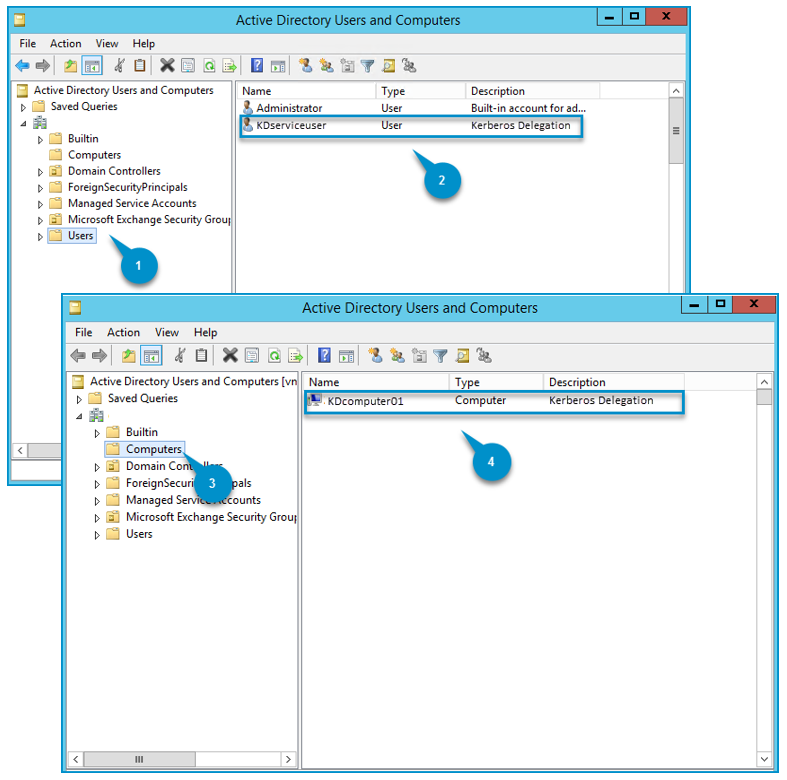
|
AD Users and Computers Legend |
Description |
|---|---|
|
1. Users folder |
Use the Users folder to open, create, or select a service account user for Kerberos Delegation. |
|
2. Service Account User |
Use the Service Account User properties to configure Kerberos Delegation. |
|
3. Computers folder |
Use the Computers folder to open, create, or select a computer(s) for Kerberos Delegation. |
|
4. Computer |
Use the computer properties to configure Kerberos Delegation. |
See also
Configuring Windows for Kerberos Delegation
Applying Kerberos Delegation to a Network Share Folder Workflow